What is Log360 ?
Log360 is a software that offers a one-stop solution for all your log management and network security challenges.
What is Log360 for?
Log360 combines the capabilities of all log management tools and offers full control over the network. It offers the opportunity to control your public cloud infrastructure from a single console.
How Log360 works?
You can track, monitor, archive and analyze your log management, servers and network in an integrated way.
Log360 Versions
You can get an offer for Log360, you can contact for demo request.
Use Cases
Organizations’ vulnerabilities may not be understood until they are attacked. You can protect yourself from attacks by creating traps and alerts.
Why CanCloud?
CanCloud has team members who have proven their expertise in IT Compliance and Log Management with numerous projects and carry this expertise forward with Manage Engine products.
Log360 – Example Screenshots
Traditional measures are not always enough. You need to audit every critical resource in your organization. Log360’s comprehensive auditing and alerting capabilities help you quickly detect and block threats. Thus, you can easily detect and analyze breaches and prevent them.
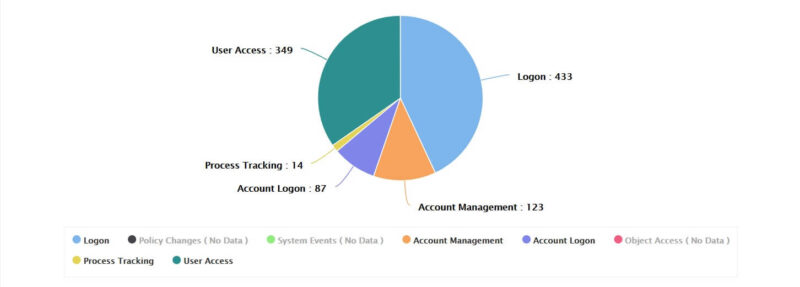
Real Time Active Directory Auditing and Reporting
Log360 collects security log data from your domain controllers to centralize Active Diretory (AD) audit information. You can track significant changes to AD objects, including users, computers, groups, OUs, security principals and GPOs, and receive real-time alerts about critical changes.
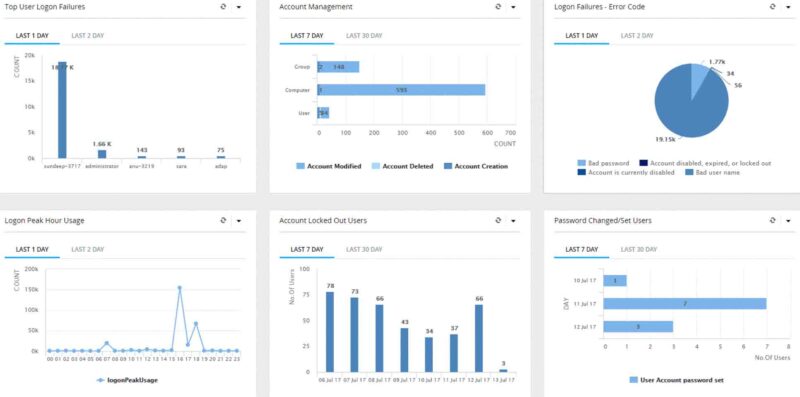
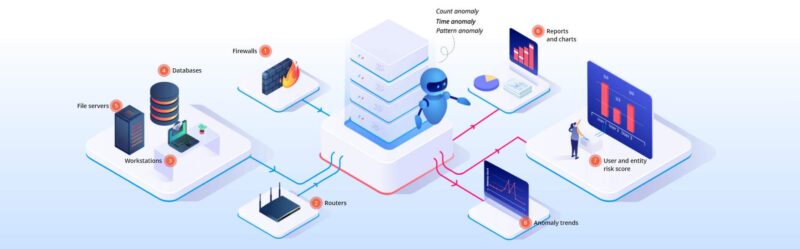
Asset and User Behavior Analytics
Improve your security posture with user and asset behavior analytics. UEBA strengthens your defense against insider threats and data breaches by using machine learning to detect behavioral anomalies.
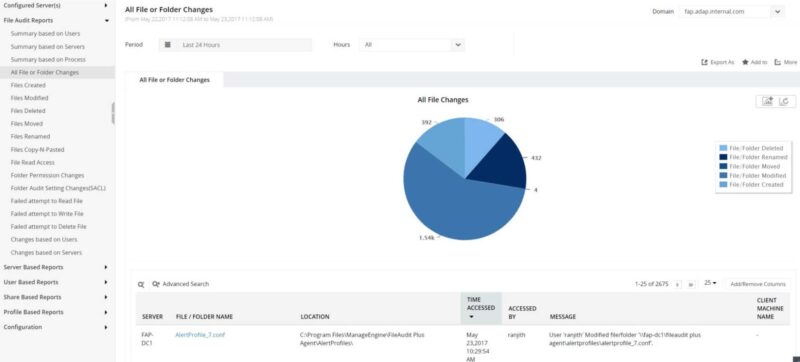
File Integrity Monitoring
Put simply: FIM is used to track and verify changes to files and folders. A FIM solution guarantees the accuracy of data by preventing unauthorized changes. Changes can be the creation, deletion, access, modification or renaming of files and folders, including failed attempts to perform any of these actions.
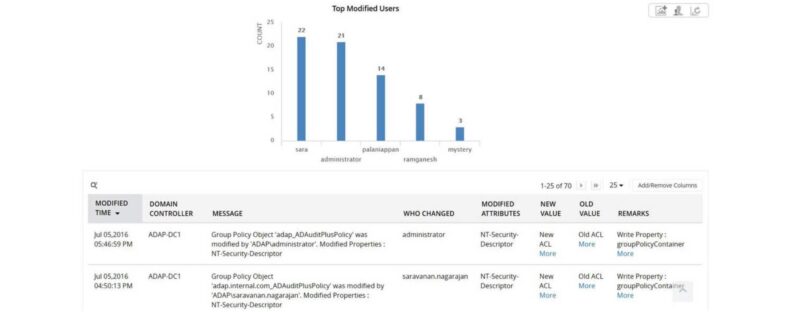
Privileged User Activity Monitoring
Privileged users have the power to make configuration changes to your network that could compromise security if left unchecked. With Log360, you can monitor login activity, including privileged user login failures, and visualize the entire user audit trail.
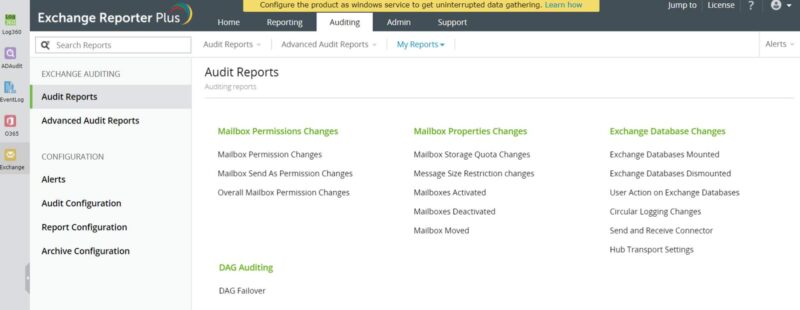
Exchange, Network, VPN, Office 365 Audit
As a security information and event management (SIEM) tool, it can report and audit Microsoft Exchange Servers with over 100 different reports for every aspect of a Network, VPN, Office 365, EndPoint Log, Exchange Server environment.