What is DataSecurity Plus ?
DataSecurity Plus’ centralized file auditing capabilities give you clear visibility into every file access and modification made by users in your file server environment.
What is DataSecurity Plus for?
DataSecurity Plus offers a two-tier solution to combat insider threats, prevent data loss and meet compliance requirements.
How DataSecurity Plus works?
Easily install, configure and run DataSecurity Plus in minutes.
DataSecurity Plus Versions
File Server Auditing – Audit, monitor and report file accesses and changes in real-time. Monitor file integrity.
Data Leak Prevention – Audit, monitor and track endpoint usage. Prevent sensitive data leaks through endpoints such as USB devices and email.
Data Risk Assessment – Discover sensitive files and classify them as PII / ePHI based on vulnerabilities. Analyze permissions, identify ROT data and more.
Use Cases
Detect and respond to critical security incidents with options to block file transfers, delete or quarantine files.
Why CanCloud?
CanCloud has team members who have proven their expertise in IT Compliance and Log Management with numerous projects and carry this expertise forward with Manage Engine products.
DataSecurity Plus – Example Screenshots
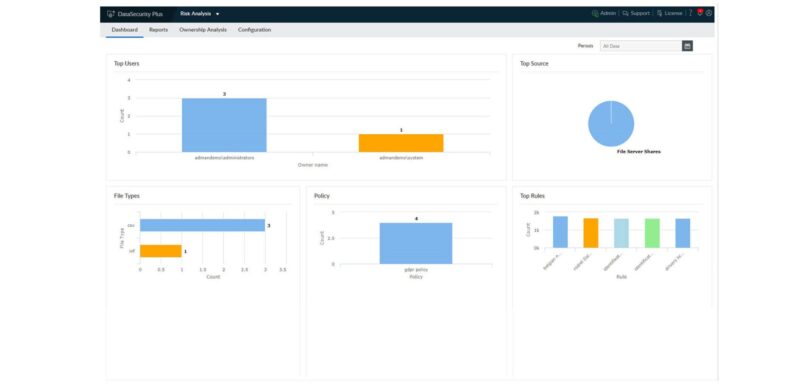
Get a snapshot of end-user activity, file activity and access trends. Who accessed what, when and from where? Focus on the most important events such as sudden permission changes, file deletions and renaming events. Identify the most active users, most accessed files and most modified files on your file server.
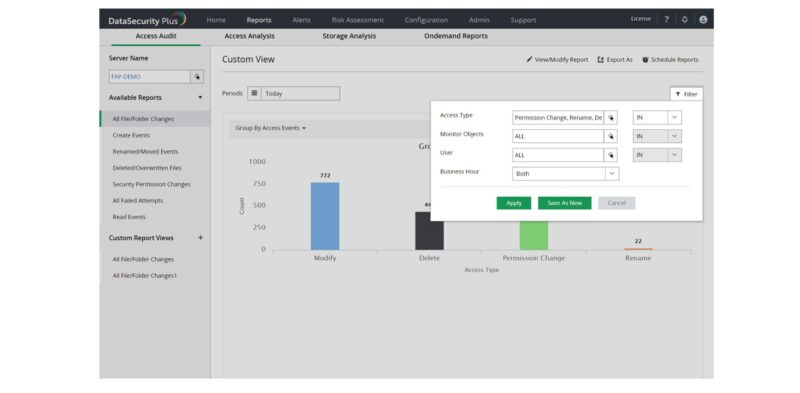
Monitor File Integrity
Trigger instant alerts when there are spikes in file or folder access or modification events. Receive real-time notifications when there are multiple failed access attempts to critical files. Monitor changes to sensitive files after business hours. Selectively monitor critical files, folders, shares and user activities.
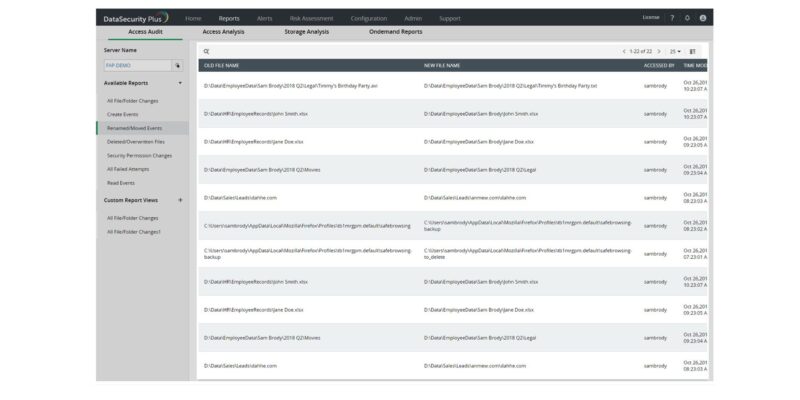
Receive Real-Time File Change Alerts
Receive real-time alerts when unauthorized changes are made to important files. Detect abuse of privileges and unusual activity by configuring threshold-based alerts to monitor user-generated events. Track source, host details and more as part of forensic analysis. Check when a file was last updated to flag unusual access after long periods of inactivity.
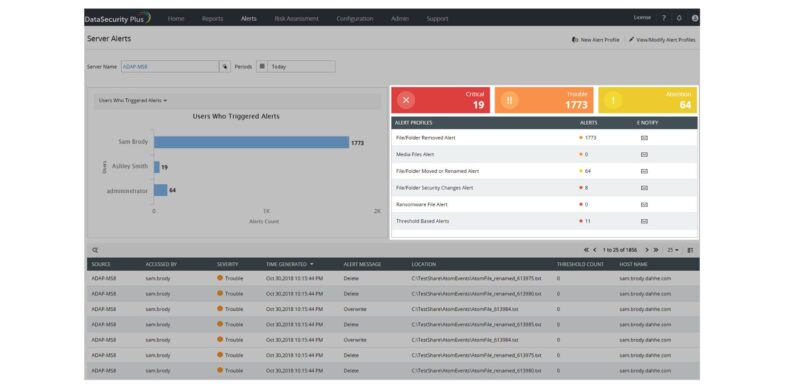
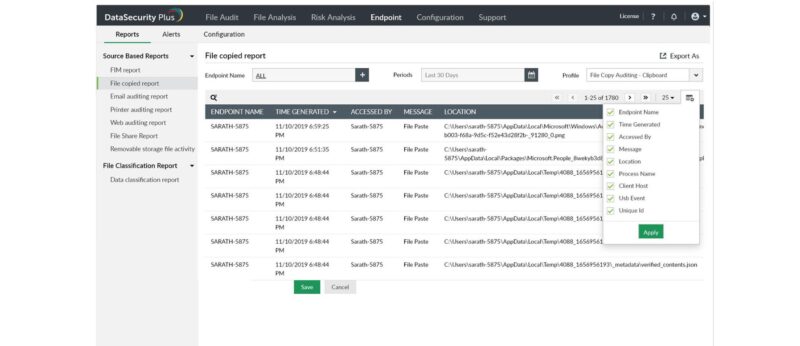
Data Leak Protection
Detect instances of unusual user behavior and stop files from leaking out via external storage devices. Create instant alerts and prevent files containing highly sensitive data such as PII or ePHI from being transported via email (Outlook). Delete or quarantine files, stop USB data transfers or choose from other predefined effective solutions to prevent data leaks.
Classify Files by Sensitivity
Automate the classification of files containing PII / ePHI to better understand which files require elevated data security measures. Enable progressive scanning of new and recently modified files to reduce data discovery scan times and ensure there are no blind spots where PII can be hidden. Analyze the risk associated with files by viewing details on the amount and type of personal data they contain.