What is PAM360 ?
Privileged Access Management (PAM), a subsection of Identity and Access Management (IAM), is a solution that provides organizations with better control and monitoring capability to decide who can have privileged access to a computer or information system.
What is PAM360 for?
It enables defining user roles, granting the necessary privileges or access rights for the defined roles, distributing user information and access permissions to all devices and systems that enforce access rights in organizations, and tracking privileged user activities & analyzing them to detect anomalies.
How PAM360 works?
PAM360 integrates with AD and synchronizes all users, groups, computers and memberships. It then automatically resets the passwords of the users on the computers at certain intervals. In order to perform these operations, it needs an agent to be installed on the servers.
PAM360 Versions
Subscription
Enterprise Edition (10-200 admin options)
Enterprise Edition Multi Langauge (10-200 admin options)
Perpetual
Enterprise Edition (10-200 admin options)
Enterprise Edition Multi Language (10-200 admin options)
Use Cases
Using PAM360, IT administrators can centrally create users, assign them specific roles and define access levels. Furthermore, PAM360’s comprehensive auditing mechanism helps track who accessed what and when, thus ensuring accountability in a multi-member environment.
Why CanCloud?
CanCloud has team members who have proven their expertise in IT Compliance and Log Management with numerous projects and carry this expertise forward with Manage Engine products.
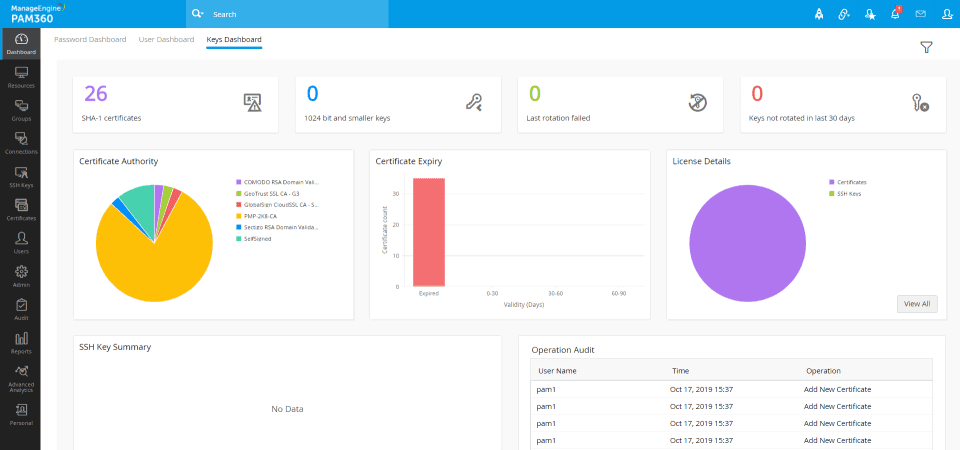
PAM360- Example Screenshots
Monitor the health status of certificates on servers that are used to access critical services. You can take action by identifying expired or improperly adapted certificates in advance.
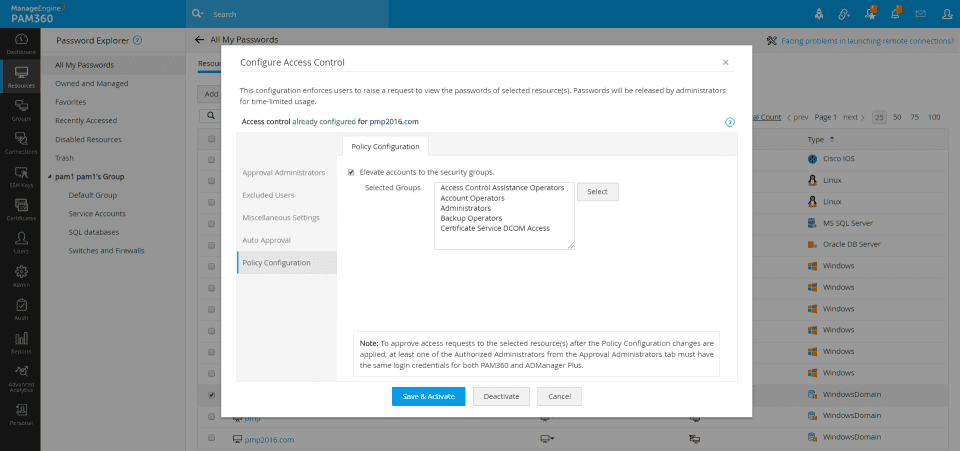
Access Permissions
Meet requests autonomously by tailoring computer and resource-based password access permissions to groups.
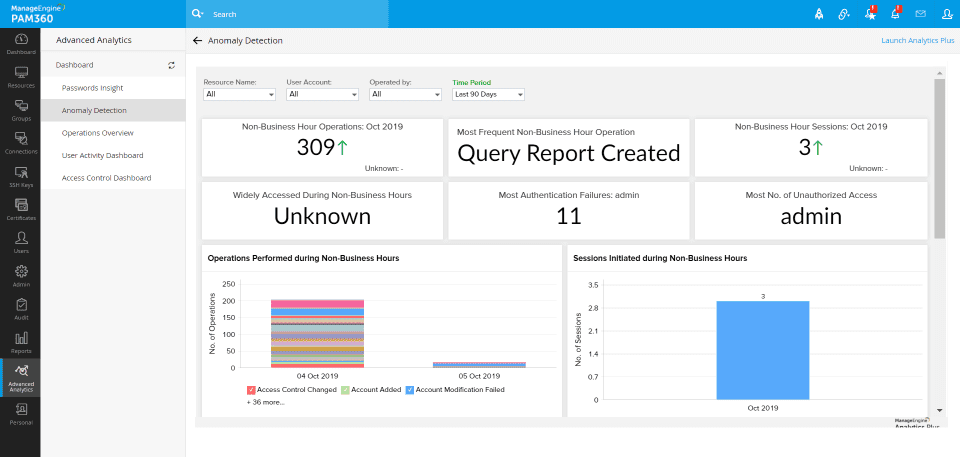
Anomaly
You can track out-of-hours transactions by detecting anomalies.
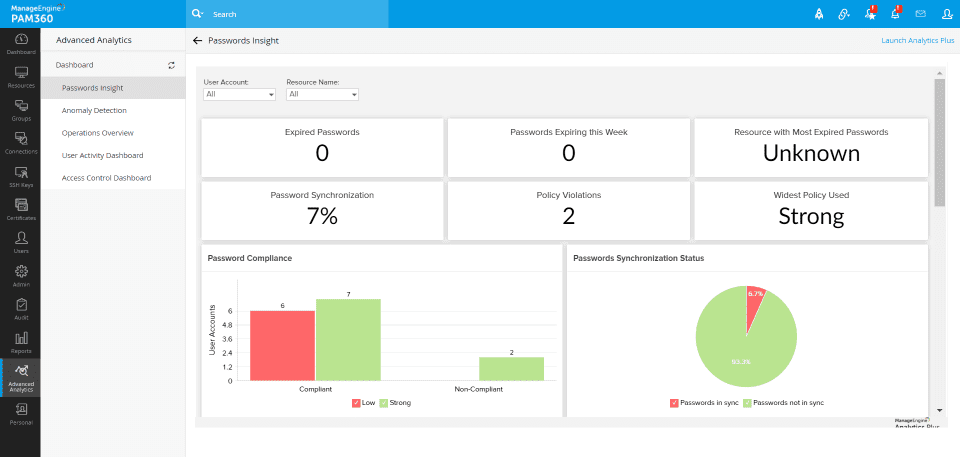
Password Analysis
You can access views about your passwords. You can see analyzes such as expired passwords, password compatibility, policy violations from this screen.
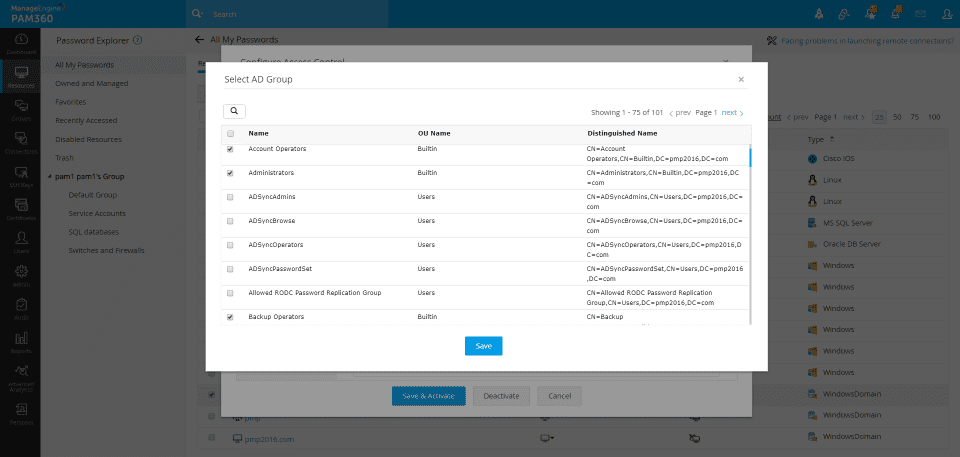
AD Groups
Provide group-based password and resource access by synchronizing Active Directory groups regularly.